Using Remote Asset Bundle in Unity3D framework really safe?
Introdution
Introdution
If you are a mobile application developer, you may be interested in exposing sensitive information from your application because of decompilation a mobile app such as Android app is not too difficult.
A friend of mine recently developed an Android application using Unity framework, it can hide code by downloading the required modules from a trusted-server at the runtime.
I really doubt this method, so I try to reverse this app to obtain the hidden code. And in this article, I will describe my work process.
You can download the APK file here. Notice this file is not the original version, it was modified to fit the article.
Analysis
Running
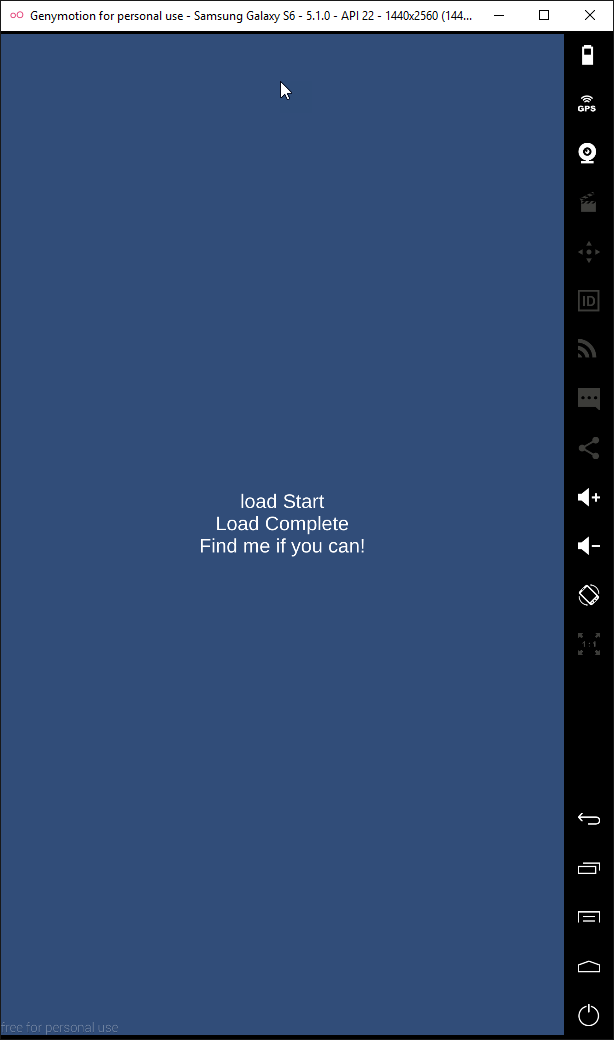
When running the application on an Android Emulator, you will see results like bellow.
Static Testing
In Unity Framework, the main code is written by C# language and compiled to a dll file. It’s compressed in the the binary file. After extract the apk file, we can see it at: /assets/bin/Data/Managed/Assembly-CSharp.dll
We easily decompile a dll written in C# by using decompilers such as dnspy, ilspy or dotpeek…
At line 39, the app loads Component ExtendModuleActivity
At line 40 and 41, displaying the content of the Component above to screen. It is “Find me if you can!” string that we have seen when runing the app.
So, where is ExtendModuleActivity? I haven’t seen it in the decompiled code. I assume that the decompiler is not effective and it does not show the source code completely
Dynamic Testing
I suspect the app downloaded required modules via HTTP, so I do some configs to force this app goes through a HTTP Proxy (such as ZAP, BurpSuite …) to know what it actually does. Note that you make sure your proxy can sniff the HTTPS Request by trusting Proxy’s Certificate in Android Client.
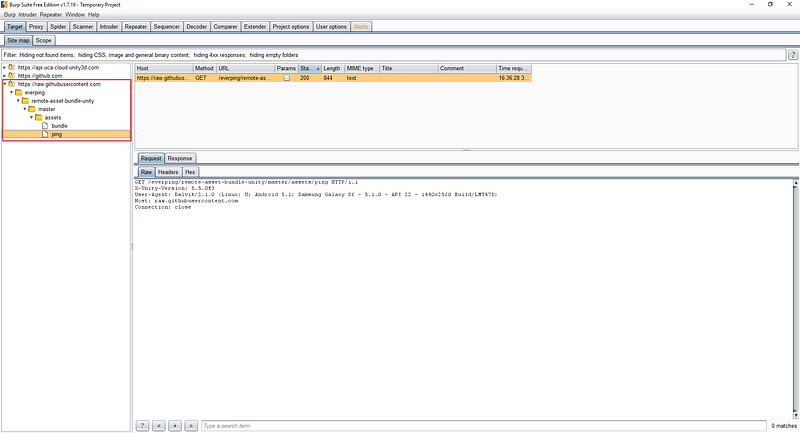
Then open the app and observe at the proxy
This app downloaded two resource from a remote server:
https://raw.githubusercontent.com/everping/remote-asset-bundle-unity/master/assets/ping
https://raw.githubusercontent.com/everping/remote-asset-bundle-unity/master/assets/bundle
The first resource is a text file that contains the content that appears on the screen, and bundle seems to contain ExtendModuleActivity that we are looking for.
In Unity Framework:
An AssetBundle is a collection of assets and/or scenes from a project saved in a compact file with the purpose of being loaded separately to the built executable application.
AssetBundles can contain scripts as TextAssets but as such they will not be actual executable code.
Extract the Bundle
I found a pretty good tool to extract bundles called Unity Assets Bundle Extractor
Load our bundle to UABE and view its information
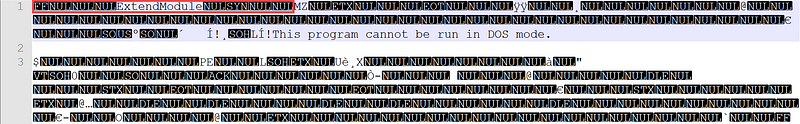
Then Export Raw to obtain the bytecode. Using an editor / hex editor, we can realize that it is PE File (beginning with MZ), but was inserted into the previous another section. We just remove this section to restore PE header file.
The rest is decompiling the new file, and this is what we are looking for :)
Conclusion
As you can see, securing applications is not an easy task. Using Remote Asset Bundle is not a perfect way to hide your source code in Unity Framework, and in addition it is appropriate only when your application requires an internet connection. This article does not go into how to prevent attacks, I just hope it can be to raise awareness about some risks in your application. Good luck!
P/s: Maybe I will implement this technique into a CTF challenge in the future.